Cyber wars: the silent battles being waged on your business and how to beat them
By Alison Baker and John Gray
The ever-evolving nature of cyber threats has made it difficult for even the most sophisticated cyber security systems to detect and prevent attacks. The average global cost to remediate a ransomware attack rose to almost AU$2.5 million this year, more than double 2020’s average. Data breaches collectively exposed over 36 billion records. The occurrence of cyber security breaches continues to increase globally, and Australia is no exception.
The Australian Cyber Security Centre (ACSC), in its 2021 report (ACSC Report), highlighted the gravity of this emerging problem. During FY2020-21, the ACSC received more than 67,500 cyber crime reports, an increase of 13% from the previous year. Total losses reported from cyber crime exceeded $33 billion.
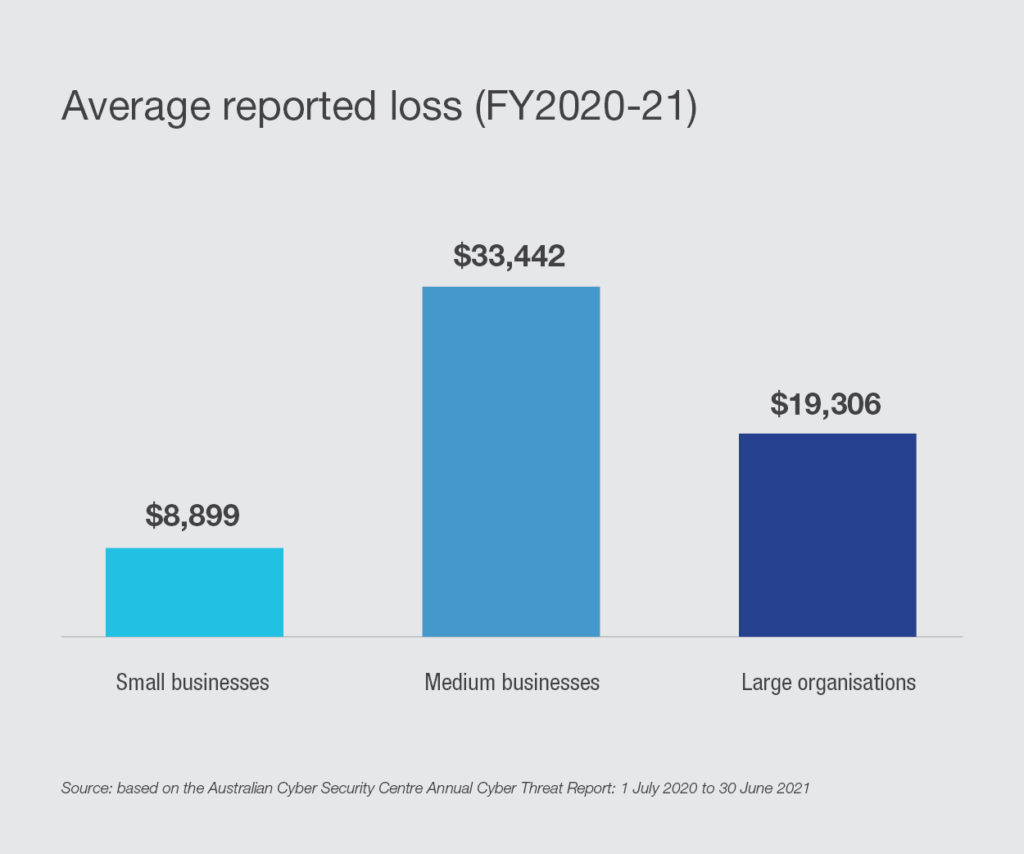
Of significant alarm is the increased proportion of ‘substantial impact’ incidents, cases that result in more catastrophic losses for the victims. The pandemic acted as a catalyst in FY2020-21, and malicious actors used it to target vulnerable users. The ACSC Report stated that the average reported loss was $8,899 for small businesses, $33,442 for medium businesses and $19,306 for large businesses.
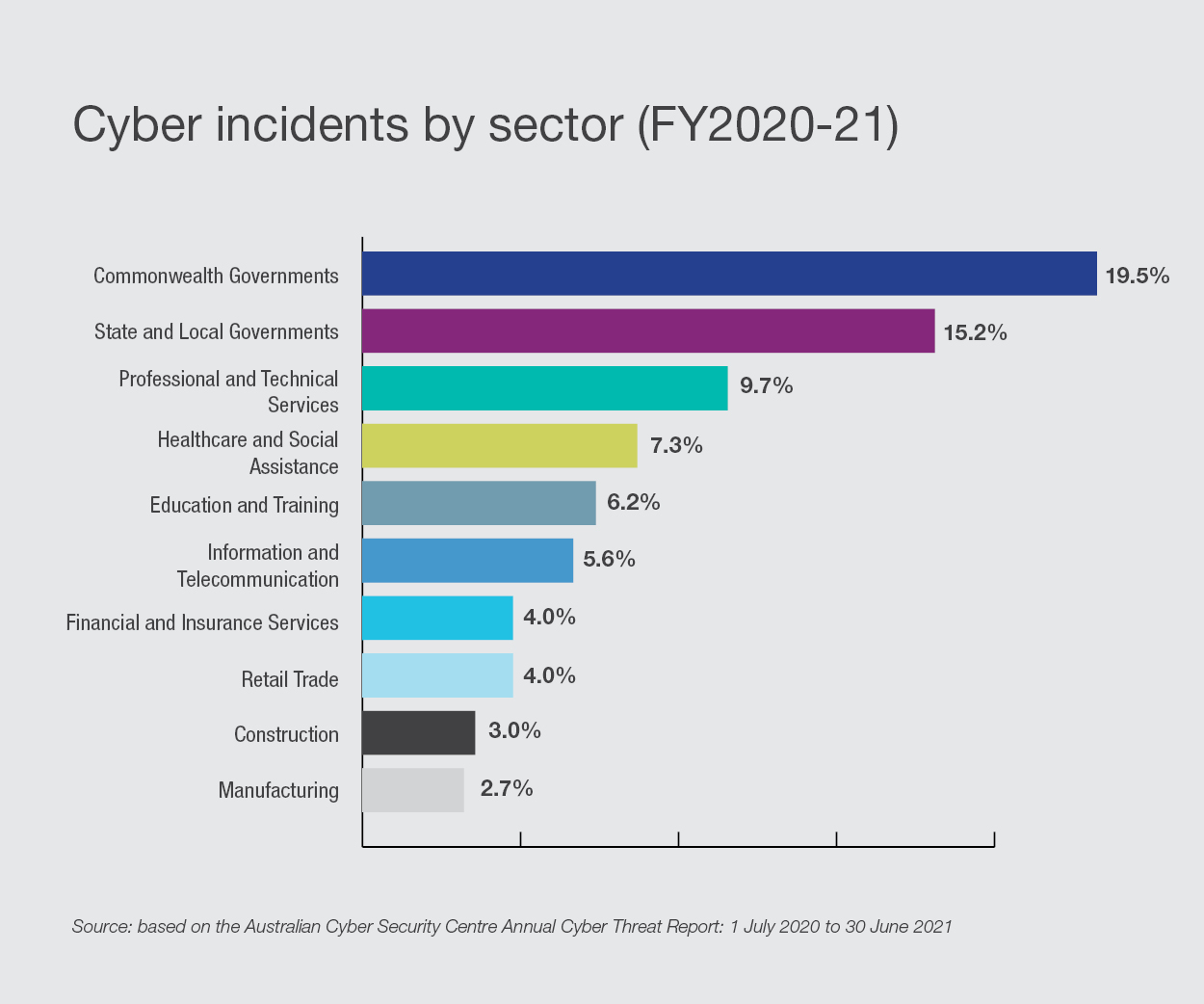
While no industry was immune from the cyber attacks, the ACSC reported that around a quarter of the incidents targeted Australia’s critical infrastructure and government-controlled services. Essential services, such as healthcare, food distribution and energy, were disrupted. Attacks in the education and training sector also continued to increase during the pandemic. The chart below shows the distribution of the attacks across different industries and sectors.
Ransomware attacks continue to be the most significant cause of concern. A 15% increase in ransomware attacks was reported by the ACSC, with the average demand for ransoms varying from a few thousand to a few million dollars. Supply chain attacks are also on the rise, both in Australia and worldwide, and many organisations are overhauling the way they communicate with their partners.
Business email compromise has remained a major threat, especially as more and more Australians work remotely. The ACSC reported the average loss from an email compromise incident is now over $50,600, which is more than one-and-a-half times higher than the figure from the previous year. In addition, fraud (23%), online shopping scams (17%) and online banking breaches (12%) were among the top reported cyber crimes.
The process of preventing, detecting and addressing cyber attacks requires constant improvement. As malicious actors use the dark web to grow their numbers and transform into coordinated groups, organisations need to upgrade their capabilities at the same, if not higher, pace. Companies should consider cyber security costs not as an operational expense but as a critical investment to ensure business continuity. The ACSC published over 40 step-by-step guides, 27 alerts and 12 advisories during the year. It has never been more important for businesses to embrace the highlighted actions.
Once aware of a cyber attack, organisations need to consider whether any confidential or personal information they hold has been compromised and what containment and remedial steps they need to take to minimise any damage or harm as a result. A data breach may trigger legislative and contractual notification obligations – obligations to notify the Australian Information Commissioner and impacted individuals where personal information has been compromised and there is a risk of serious harm as a result, and obligations under contract to notify clients, suppliers and other third parties where the security of their commercially sensitive and confidential information has been breached. Businesses may also consider reporting cyber crimes to the ACSC through the ReportCyber website.
Finally, businesses should review their network infrastructure to identify vulnerable entry points, and take steps to address the weaknesses. Steps such as cyber security audits, third-party evaluations and ethical hacking exercises can help identify vulnerabilities.
While the emphasis should be on early detection, unfortunately, cyber attacks are often detected long after they occur. For instance, the global average time to identify a breach is 206 days, and the average time to contain it is 73 days. That is long enough for the perpetrators to inflict all sorts of damage. To minimise the impact, incident response, business continuity planning and disaster recovery plans should not just be prepared but must be regularly tested. They can be the difference between an operational business and a bankrupt business post-attack.
Based on the findings of the ACSC Annual Cyber Threat Report and contemporary cyber attack trends, it is critical for all users, groups and organisations to remain vigilant and continuously increase their cyber security awareness. Given the magnitude of losses that even a single reckless click can cause, attention should be paid to upgrading security systems, providing training to employees, having a comprehensive data breach response plan and well-equipped data breach response team in place, conducting security assessments and monitoring cyber security updates.
For help with your organisation’s privacy policy and keeping your information secure, please contact Alison Baker or John Gray.